
As industries undergo rapid digital transformation, the reliance on custom software solutions has reached unprecedented levels facilitating tailored experiences and streamlined workflows. As organizations invest heavily in developing tailored user interfaces (UI) to meet their specific needs, they often overlook the importance of integrating robust cybersecurity measures into these interfaces. This oversight can expose systems to a spectrum of threats, from insidious data breaches to outright malicious attacks.
To address this critical issue, it’s essential to adopt a proactive approach to cybersecurity throughout the software development lifecycle, with a particular focus on UI design.Join us in this blog as we delve into the essential strategies for enhancing cybersecurity in custom software user interfaces.
Cybersecurity refers to the practice of protecting information from unauthorized access to avoid identity theft and to protect privacy. These attacks are often carried out by malicious actors with the intent to access sensitive information, change or destroy data, extort money or disrupt operations. There are many different types of cybersecurity threats such as malware, phishing attacks, social engineering , hacking and many more. Cybersecurity measures involve a layored approach that includes technology like firewalls and antivirus software, processes like password management and data handling.
Here’re the various ways in which UI elements can be exploited and can inadvertently become entry points for cyberattacks.
Login Forms : Attackers can employ credential stuffing attacks by automating the input of stolen credentials into login forms. They exploit the weak authentication methods or use brute force techniques to gain unauthorized access.
Data Input Fields : Injection attacks such as SQL injection and cross site scripting (XSS), can occur when input fields are not properly validated thus allowing attackers to inject malicious codes or commands.
User Profiles : Exploiting vulnerabilities in user profiles, attackers gain unauthorized access to sensitive information or manipulate user settings for subsequent attacks, posing significant security risks to the system’s integrity.
Phishing : Attackers may create deceptive UIs, such as fake login forms or pop-up windows, to trick users into divulging sensitive information such as usernames, passwords, or financial data.
Injection Attacks : SQL injection and XSS attacks target vulnerabilities in UI input fields that enable cyber-criminals to implant malicious code, steal data, or seize control of user sessions.
Social Engineering : By exploiting psychological manipulation techniques, attackers exploit users’ trust through deceptive UI elements, coaxing them into actions that compromise security, such as clicking on harmful links or downloading malware.
Lack of Input Validation : Ensuring robust input validation is crucial for securing applications against injection attacks. For instance, a website allowing unchecked user comments might become a target for XSS vulnerabilities.
Inadequate Authentication Mechanisms : UIs employing weak authentication measures, like single-factor authentication or easily guessable passwords, become easy prey for credential stuffing and brute force assaults.
Deceptive UI Elements : UIs that mimic genuine interfaces or display fake error messages to deceive users into disclosing sensitive information are often used in phishing attacks.
Related : What is Application Modernization?
Cybersecurity has become an indispensable aspect of software development, with user interface (UI) design plays a crucial role against cyber threats that cannot be overstated. “Security by Design” is a fundamental principle that advocates for the seamless integration of security measures across all phases of software development, including UI design. This proactive approach equips organization to effectively mitigate vulnerabilities and elevate their cybersecurity resilience.
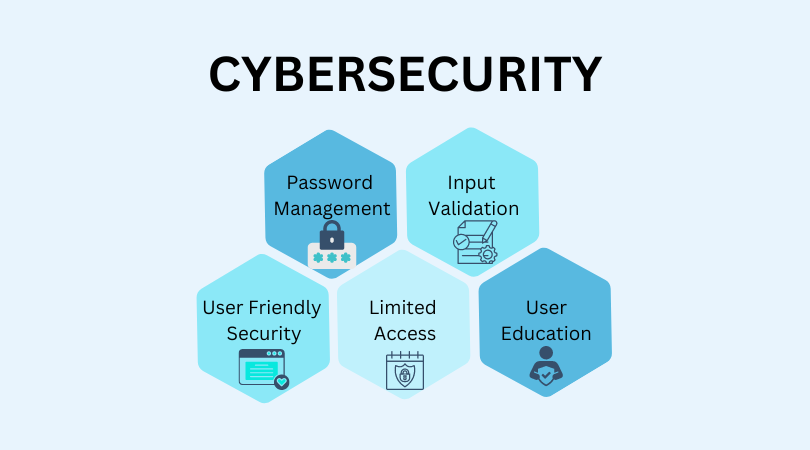
Safeguard user logins with strong password requirements (length, variety, no common patterns) and secure storage using hashing (cryptographic algorithms) and salting to protect against data breaches. Consider implementing Multi-Factor Authentication as an additional security measure, which requires users to verify their identity through multiple factors such as passwords, biometrics or one-time codes.
Enforce strict validation rules to ensure user data adheres to defined formats and prevent injection attacks like SQL injection and XSS. Furthermore, sanitize input to remove or encode potentially harmful characters, mitigating the risk of unforeseen behavior and security weaknesses.
Avoid revealing technical details or user data in error messages, as this could be for attackers. Instead, use generic messages that inform users of an error without compromising security. This minimizes the risk of attackers exploiting vulnerabilities exposed in detailed error messages.
Limit users with only the essential access. This approach, known as the Principle of Least Privilege, reduces the attack surface and minimizes potential damage from security breaches. Avoid giving unnecessary access rights, as these could be exploited for privilege escalation or sensitive data access.
Integrate security awareness modules directly within the software to educate users on best practices and common cyber threats. Complement this with comprehensive documentation detailing secure usage, potential risks, and guidance on identifying and mitigating cyber threats. This approach empowers users to contribute to a secure environment.
Robust security measures within the UI demonstrate a commitment to user data safety. This fosters trust, leading to long-term user relationships and continued engagement with your platform.
A secure UI design acts as a formidable shield against potential threats, significantly reducing the risk of data breaches, unauthorized access attempts, and cyberattacks.
A secure UI design speaks volumes about your commitment to cybersecurity, enhancing your brand reputation and fostering trust with users and stakeholders alike. Prioritizing security positions your organization as a trustworthy custodian of sensitive data.
As security becomes an ever-increasing concern for users and businesses alike, software with a robust security posture commands a premium in the marketplace. A secure UI inherently adds value to custom software by strengthening its resilience against cyber threats.
Cybersecurity is no longer an afterthought – it’s a fundamental requirement for building trust and ensuring the success of your custom software.A secure UI design fosters user confidence. By partnering with Zoondia, you ensure a user experience that prioritizes data privacy and empowers users to navigate your software with trust, giving you a competitive edge in the marketplace.
Let us help you safeguard your valuable data and create a custom software solution that inspires user confidence. Contact us today and see how Zoondia can turn your vision into a secure and thriving reality.
Leave a Reply